Thanks to Transparency Toolkit, I've been able to have a look through the whole file-tree without downloading the whole thing. Now, with any luck, I'll be able to find some proper documentation.
Side note: I've been working on cleaning up a Python script from one of the exploits in the vector-exploit repository. It modifies a given Word document with a Shockwave Flash exploit which enables downloading and executing arbitrary files. The original is rehosted here, and my partially cleaned version is here.
After some poking around through the directory tree - finding lots of data from clients like Barclays, Carrefour and the Belgian Police force - I found what I was looking for. There's a directory of manuals tailored for different personnel:
Because I was still pretty clueless as to how the whole system worked, I felt like SysAdmin was the best bet for a birds-eye-view.
The contents page alone spans 9 pages, so I didn't feel like reading the whole thing. Luckily, there's a very easy-to-understand system diagram quite early on, reproduced here:
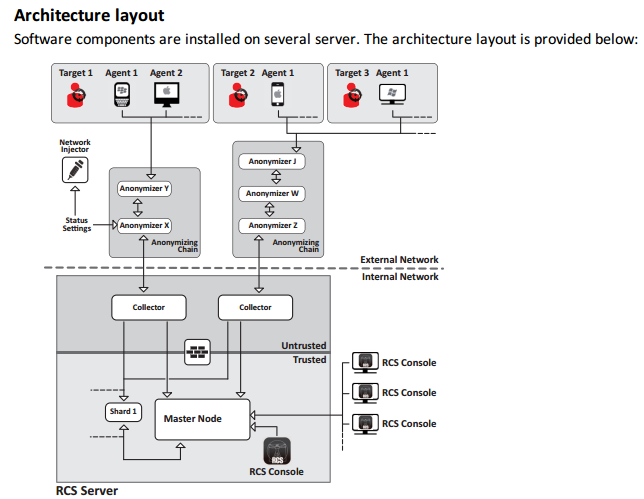
And on pages 7 and 8, there's a handy table explaining some of the terminology that confused me when looking at rcs-core.rb earlier on. Of note: an Agent is a single installation of RCS on a target's device. From the manual, an Agent's function is described like so:
"Software bugs tap and communicate the investigation
target's data and information to an Anonymizer."
I wanted to find out what a "Factory" was, and it seems like this is all the manual has to say on the subject (found in the glossary on page 111):
"A template for agent configuration and compiling."
The manual also explained a lot of the other repositories: like, for instance, RCS-Console and RCS-Collector.
It'd be fun to try to set up a whole RCS installation based on the information in the Manuals, but it's probably not viable with a budget of effectively £0 (especially with Anonymizer Chains as stipulated in the SysAdmin manual).
